Decrypting Canva’s Security Breach That Affected 139 Million User Accounts
Yet another Attack by a Hacker responsible for Cyber Threats at over 44 Companies Worldwide

If you have been a Canva user for over a year now, then on the 26th of May 2019 you would have received an email from Canva notifying you about the company being at the receiving end of a security attack. Canva was very responsive throughout, be it in taking the necessary protective measures against the attack or informing the concerned cyber crime cell.
However, at that time the attack was estimated to have only minimally impacted 139 million user accounts. It was only later on the 11th of January 2020 that it was found that the attack could have left its repercussions on as many as 4 million accounts whose passwords had also been successfully decrypted by the hacker.
But before we go further, to give you a brief background about Canva, it is one of the most popular graphic design startups that was founded in Australia in 2013. Currently it has a presence in 190 countries with 15 million users. Read on to know more about the attack and how Canva immediately responded to counter the potential damage.
Going Back To The Morning Of The Attack
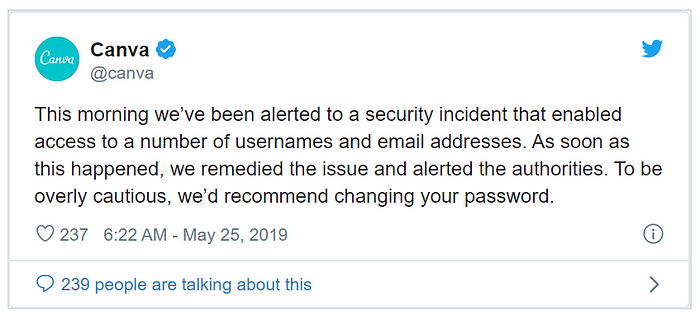
On the 24th of May 2019, a hacker who goes by the name GnosticPlayers contacted ZDNet and claimed to have breached Canva earlier that morning.
“I download everything up to May 17,” the hacker said. “
-As reported by ZDNet
The Canva attack wasn’t the first time that he/she/the group was responsible for a cyber attack. Dubsmash, MyFitnessPal, Zynga are few of the names who had previously fallen victim to GnosticPlayers’ data breaches. GnosticPlayers is infamous as a hacker who has stolen data of over 900 million users from 45 companies worldwide and put them on sale on the dark web.
But how was the Canva attack different from other attacks?
Here, the attack was discovered and stopped by Canva while it was still occurring. Canva had immediately shut its database servers on detecting the attack. But what was most surprising was the fact that after the attack was stopped, the hacker directly contacted a journalism group (ZDNet) and admitted to having committed the crime.
“It’s common to brag about hacks on dark web forums, but contacting journalists directly and spreading awareness like this is almost unheard of,” Oz Alashe, CEO of intelligent cyber security awareness platform CybSafe, told Verdict.
This bold measure on the part of the hacker was considered by many to be a ploy to steer more sales of the stolen user accounts that he had put for sale on the dark web.
What was compromised in the attack?
- The profile database of 139 million users was accessed. This contained usernames, email ids, public profile ids.
- Encrypted passwords using bcrypt hashing algorithm. bcrypt is still considered to be one of the most secure algorithms.
- A claim of access to the OAuth login tokens of those users who had logged in using Google. (OAuth tokens are what applications use to make requests on behalf of the user for the authorization of the specific application.)
- Limited viewing of card details and payment data. Fortunately for Canva, it never stores complete credit card information in one place. Therefore even though the attacker might have viewed these files momentarily, they couldn’t have used it for carrying out payments.
Why were the users not thought to be at much risk?
- Since the passwords had been first salted and then protected with a hashing function called bcrypt, it was considered then that even though the attackers had access to the hashed password they would never be able to decrypt them and recover the original password. bcrypt is one of the strongest hash algorithms there is since its iteration count can be dynamically increased with time to make it slower and thus resistant to brute force attacks.
- The OAuth tokens too were encrypted using an algorithm called AES128 and the keys for the same were stored in another separate secure location. There was no evidence that those keys from that location were accessed. And without the keys, the tokens alone wouldn’t prove to be of much use to the attacker.
What was Canva’s Response To the Attack?
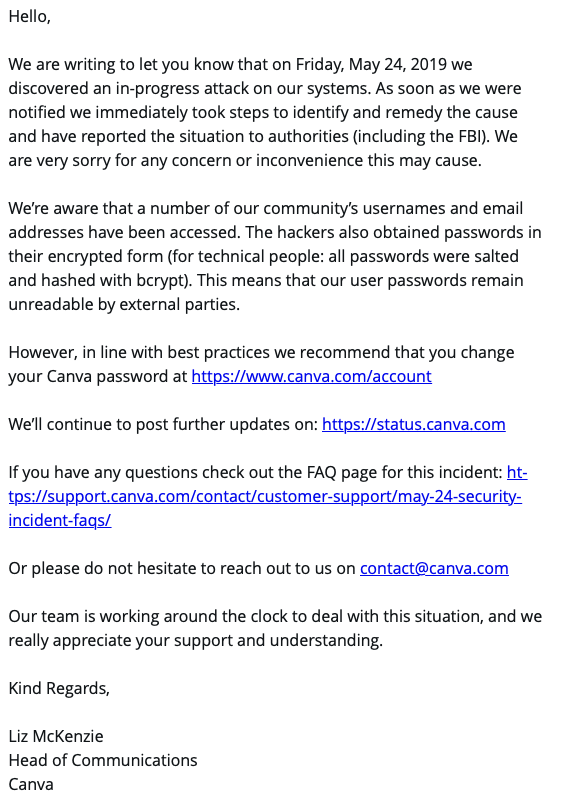
I too was a Canva user at the time of the breach and I still am. I received the following mail from them as did its other customers on the 26th of May, 2019.
Unexpected Turn Of Events…
It was only on the 11th of January 2020, 7 months after the attack that the company became aware that the hacker had been able to decrypt the passwords of as many as 4 million Canva accounts out of the 139 million accounts that had been compromised by the breach. It sent Canva into damage control mode once again.
Canva promptly notified all its users of the attack and asked all those with unencrypted passwords to change their passwords immediately by sending out necessary emails containing a set of guidelines for setting the new password. On the 12th of January 2020, Canva forcibly reset the password of all those who hadn’t changed their passwords yet and sent out emails about the same to its users.
What’s the Current Situation?
In spite of all the storm that Canva weathered, to date, it continues to be one of the fastest-growing tech companies. In fact, since the attack, its Alexa website traffic rank shot up substantially and it was featured among the Top 200 most popular websites. Canva is currently valued at a massive sum of $3.2 billion. It remains a favorite among its users who are looking to build quick and attractive designs, logos, and posters.
However, this incident also brought to light a very essential issue for budding businesses and startups — that however good their product might be, if they don’t cultivate healthy cyber security practices it will be difficult for them to survive going ahead.
That’s all! Thanks for reading the entire way! Do leave your feedback.
You can also connect with me on:
LinkedIn: https://www.linkedin.com/in/spreehadutta/
Twitter: https://twitter.com/DuttaSpreeha
GitHub: https://github.com/Spreeha
Mail: spreehadutta@gmail.com

